Networks form the backbone of modern computing, connecting devices, services, and users across the globe. As networks grow in complexity, ensuring their security and stability becomes increasingly challenging. This is where Nmap (Network Mapper) comes into play. Nmap is a powerful open-source tool used for network exploration and security auditing. In this comprehensive guide to nmap, we’ll delve deep into Nmap, exploring its features, usage, and various scan examples, including the Nmap Scripting Engine (NSE).
Introduction to Nmap
Nmap, developed by Gordon Lyon (also known as Fyodor Vaskovich), is a versatile network scanning tool used by security professionals, system administrators, and enthusiasts alike. It allows users to discover hosts, services, and open ports on a network. Nmap’s flexibility and extensibility make it a staple in the arsenal of network administrators and penetration testers.
Installation
Nmap is available for various operating systems, including Linux, Windows, and macOS. Installation methods vary depending on the platform.
Linux
On Debian-based systems (e.g., Ubuntu), you can install Nmap using apt:
sudo apt-get install nmapOn Red Hat-based systems (e.g., CentOS), you can use yum:
sudo yum install nmapWindows
For Windows users, Nmap can be downloaded from the official website (https://nmap.org/download.html). The installer provides a graphical interface and command-line tools.
macOS
On macOS, you can install Nmap using Homebrew:
brew install nmapBasic Usage
Nmap’s basic syntax follows the pattern:
nmap [Scan Type(s)] [Options] {target specification}Here’s a breakdown of the components:
- Scan Type(s): Defines the type of scan to perform.
- Options: Additional parameters that modify the scan behavior.
- Target Specification: Specifies the target(s) to scan, such as IP addresses, hostnames, or CIDR notation.
Host Discovery
Before conducting port scans, it’s crucial to identify active hosts on the network. Nmap offers several techniques for host discovery.
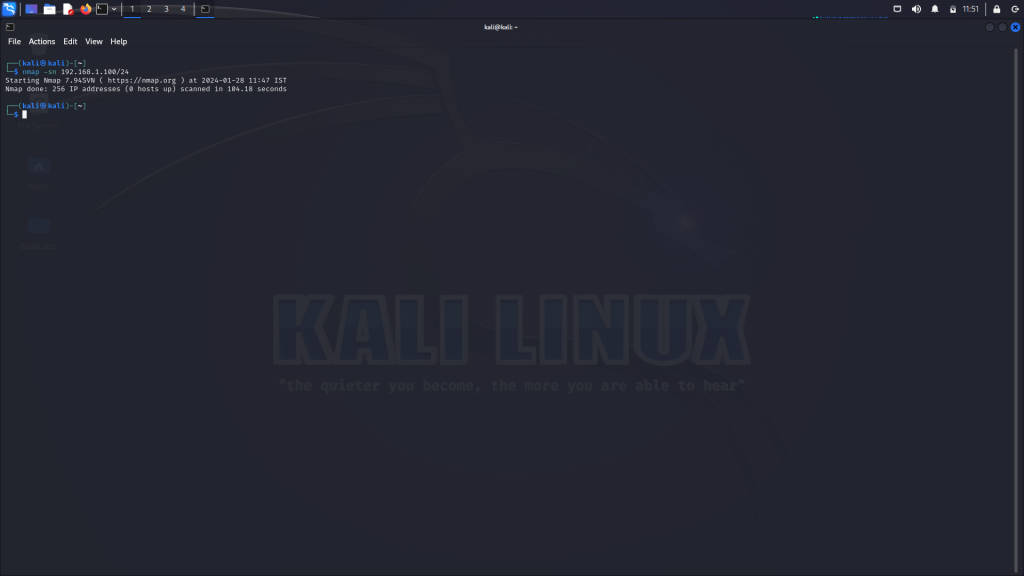
Ping Scan (-sn)
The ping scan (-sn) is a quick way to determine which hosts are online without performing a port scan:
nmap -sn 192.168.1.100/24This command scans the specified network range and reports back with a list of active hosts.
TCP SYN Scan (-sS)
The TCP SYN scan (-sS), also known as stealth scan, sends SYN packets to the target ports and analyzes the responses to determine the port state.
nmap -sS 192.168.1.100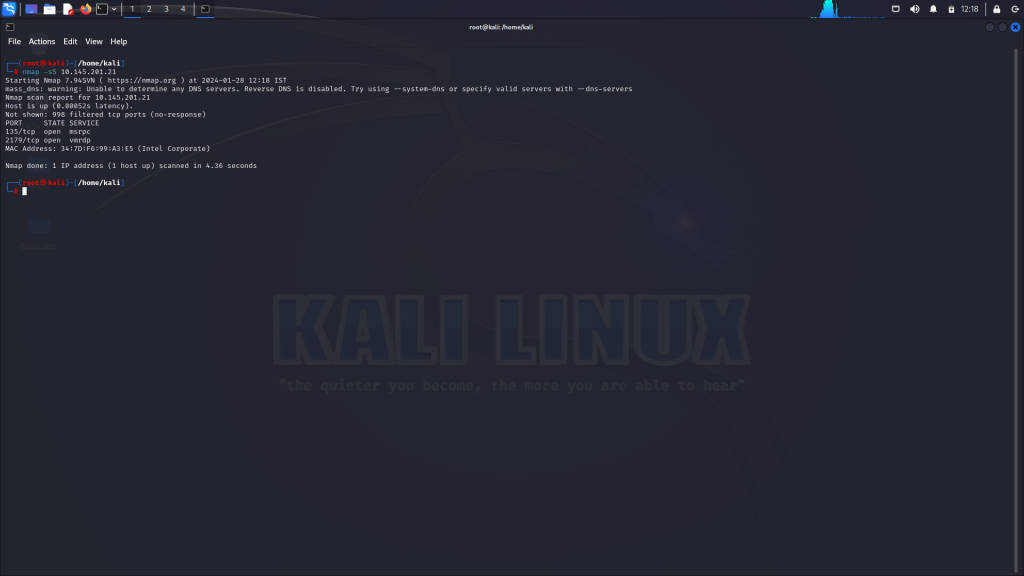
Port Scanning Techniques
Port scanning is the process of probing a host for open ports and services. Nmap provides various scan techniques to achieve this.
TCP Connect Scan (-sT)
The TCP connect scan (-sT) establishes a full TCP connection to each port to determine its state:
nmap -sT 192.168.1.100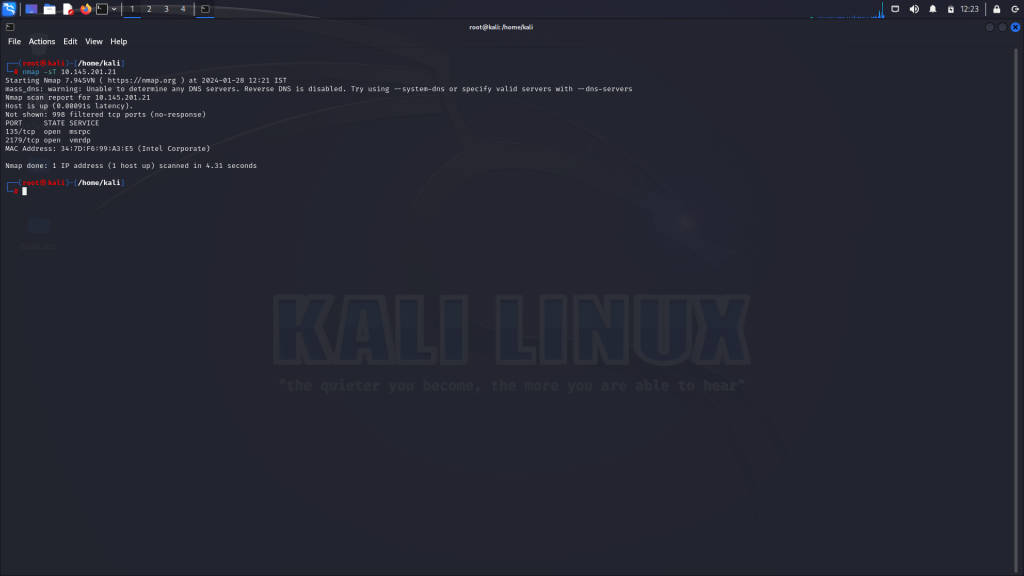
UDP Scan (-sU)
The UDP scan (-sU) sends UDP packets to selected ports and analyzes the responses:
nmap -sU 192.168.1.100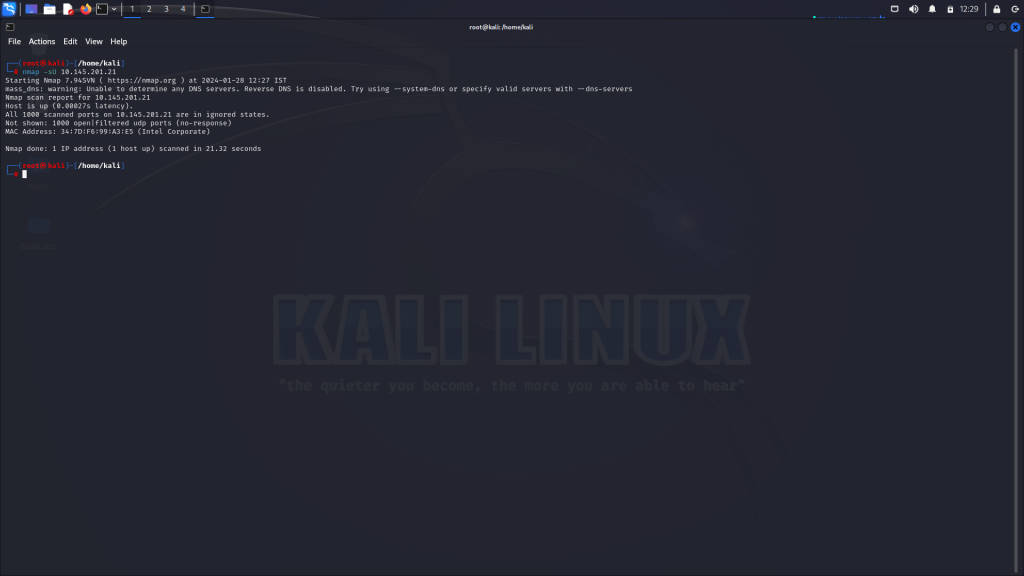
Service and Version Detection
Nmap can identify the services running on open ports and attempt to determine their versions.
Service Version Detection (-sV)
The service version detection (-sV) probes open ports to identify the services and their versions:
nmap -sV 192.168.1.100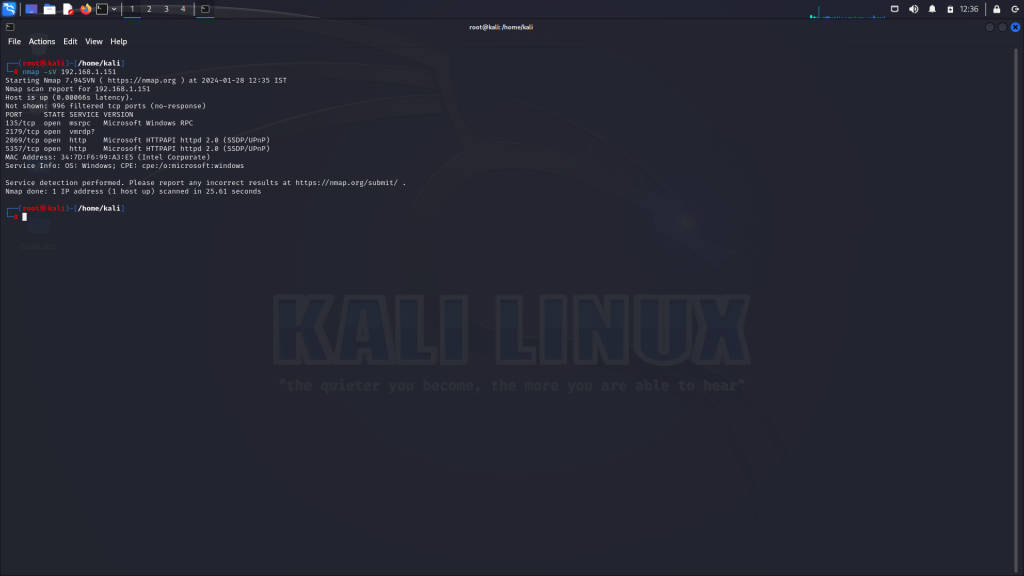
Operating System Detection
Nmap can attempt to identify the operating system of the target host based on various characteristics.
OS Detection (-O)
The OS detection (-O) feature analyzes responses from the target to infer its operating system:
nmap -O 192.168.1.100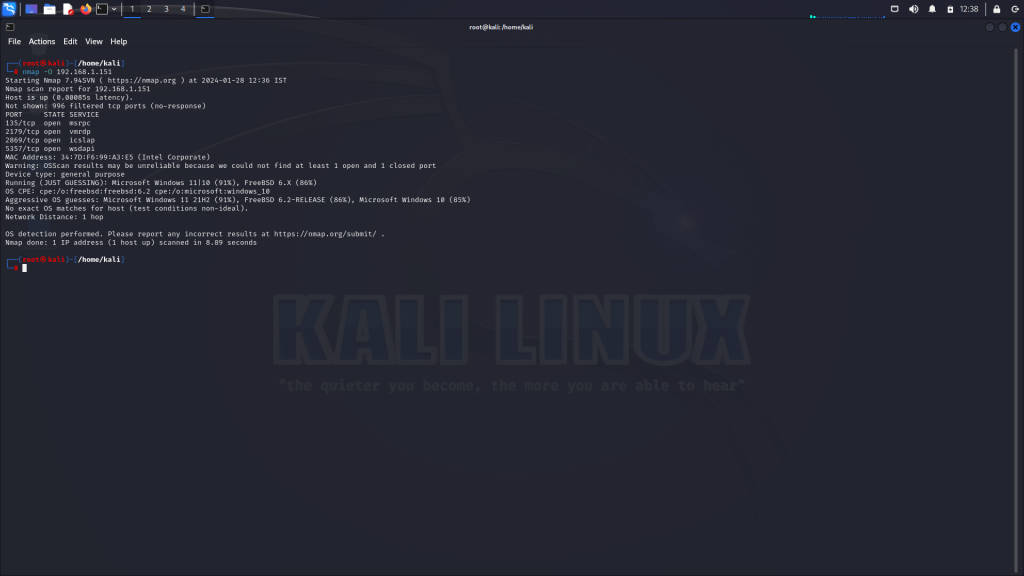
Scripting with Nmap
Nmap’s Scripting Engine (NSE) allows users to extend its functionality by running scripts for various purposes, such as vulnerability detection and network discovery.
Script Scan (-sC)
The script scan (-sC) enables a set of default scripts to be executed against the target:
nmap -sC 192.168.1.100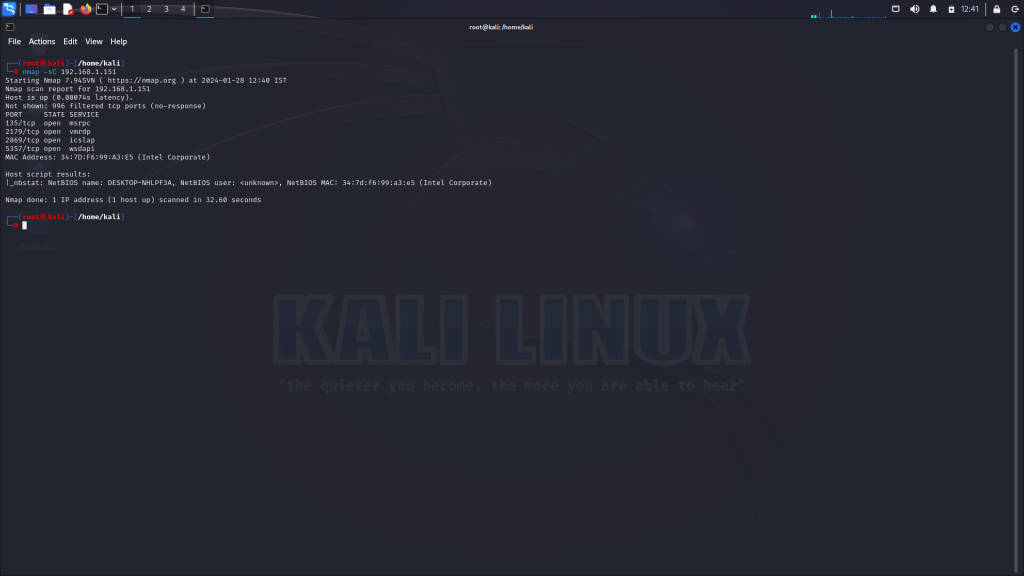
Advanced Scan Techniques
Nmap offers advanced scan techniques to bypass firewalls, evade detection, and gather more detailed information.
Fragmented Packet Scan (-f)
The fragmented packet scan (-f) splits packets into smaller fragments to bypass firewall rules:
nmap -f 192.168.1.100Nmap Output Formats
Nmap provides various output formats to suit different needs, including interactive, XML, and grepable formats.
XML Output (-oX)
To save scan results in XML format:
nmap -oX scan_results.xml 192.168.1.100Nmap Scripting Engine (NSE)
Nmap’s Scripting Engine (NSE) empowers users to automate tasks and extend Nmap’s capabilities through custom scripts.
The NSE provides access to a vast library of pre-written scripts for a wide range of tasks, including:
- Vulnerability detection
- Service enumeration
- Host discovery
Custom NSE scripts can be written in Lua and leveraged during scans to gather additional information or perform specific actions.
NSE Script Examples
Here are a few examples of NSE scripts:
HTTP Enumeration
This script enumerates information about web servers, including supported methods and headers:
nmap --script=http-enum <target>FTP Anonymous Login Check
This script checks if anonymous login is allowed on an FTP server:
nmap --script=ftp-anon <target>SMB Enumeration
This script enumerates shares, users, and other information from SMB servers:
nmap --script=smb-enum* <target>Nmap Tips and Best Practices
- Be mindful of network policies: Ensure you have proper authorization before scanning networks.
- Use quiet mode (-q): Suppress unnecessary output to improve readability.
- Experiment with options: Explore Nmap’s extensive options and parameters to tailor scans to your requirements.
- Stay updated: Regularly check for Nmap updates and new script releases to leverage the latest features and improvements.
Conclusion
Nmap is a powerful tool for network exploration, security auditing, and vulnerability assessment. Its versatility, extensibility, and robust feature set make it indispensable for both
novice and seasoned professionals in the field of network security. By mastering Nmap’s capabilities and employing best practices, you can gain valuable insights into network infrastructure, identify potential vulnerabilities, and fortify defenses against malicious threats.
This guide has provided an extensive overview of Nmap’s features, usage, and advanced techniques, including the Nmap Scripting Engine (NSE) and examples of custom scripts. With practice and exploration, you can harness the full potential of Nmap to safeguard networks and ensure their integrity in an ever-evolving digital landscape.







