In the ever-evolving landscape of cyber threats, ransomware has emerged as a particularly pernicious strain. By encrypting a victim’s files and demanding a ransom for their decryption, ransomware can cause significant financial and operational disruption. One such ransomware variant, Kasseika, has recently come to light, and it stands out for its cunning use of antivirus drivers to disable competing security software.
What is Kasseika Ransomware?
Kasseika ransomware was first identified in April 2023, and it has since targeted a wide range of victims, including individuals, businesses, and even government organizations. The ransomware is written in the Rust programming language, which makes it relatively lightweight and efficient.
Kasseika’s Devious Tactic: Abusing Antivirus Drivers
One of the most notable features of Kasseika is its use of a kernel-mode driver. This driver allows the ransomware to gain privileged access to the system, which makes it more difficult to detect and remove. The driver also enables Kasseika to disable other antivirus programs that are running on the system, thereby creating a window of opportunity for the ransomware to encrypt files without interference.
Security researchers have analyzed Kasseika’s driver and found that it exploits a vulnerability in a legitimate driver called “VBoxDrv.” This vulnerability allows the Kasseika driver to load into the kernel with elevated privileges. Once loaded, the Kasseika driver can then terminate the processes of other antivirus programs.
Kasseika’s Encryption Techniques
In addition to its use of antivirus drivers, Kasseika ransomware also employs a number of other techniques to evade detection and removal. For example, the ransomware can hide its files and processes, and it can also tamper with system registry entries.
According to security researchers, Kasseika ransomware uses a combination of symmetric and asymmetric encryption to encrypt files. The symmetric encryption algorithm, ChaCha20, is used to encrypt the contents of files, while the asymmetric encryption algorithm, RSA, is used to encrypt the symmetric encryption key. This makes it very difficult for victims to decrypt their files without paying the ransom.
The Attack Flow of Kasseika Ransomware
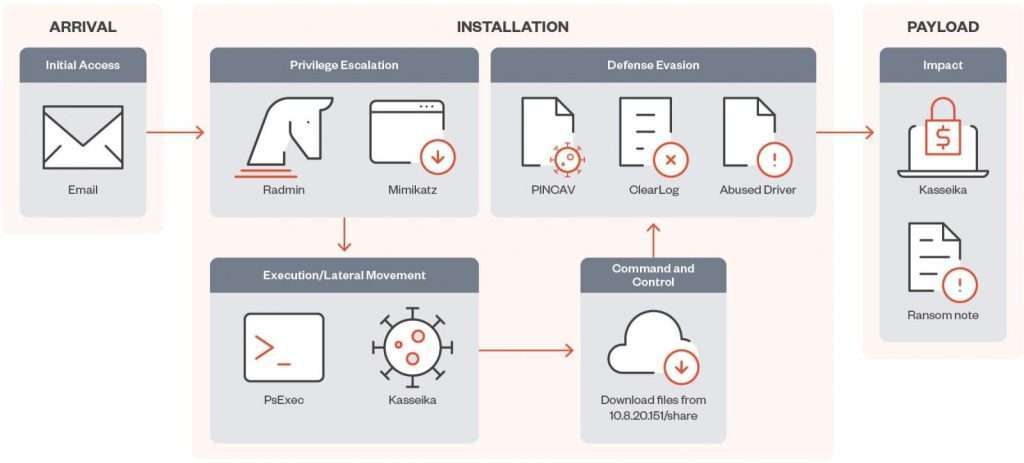
The following is a typical attack flow of Kasseika ransomware:
- Infection: The victim clicks on a malicious link or attachment in an email, or downloads a file from an untrusted source.
- Delivery: The malicious payload is delivered to the victim’s computer.
- Driver Installation: The ransomware installs its kernel-mode driver.
- Antivirus Disabling: The driver exploits the vulnerability in the VBoxDrv driver to load into the kernel with elevated privileges. Once loaded, the driver terminates the processes of other antivirus programs.
- File Encryption: The ransomware begins to encrypt the victim’s files.
- Ransom Note: The ransomware leaves a ransom note on the victim’s computer, demanding a payment in cryptocurrency to decrypt the files.
The Impact of Kasseika Ransomware
Kasseika ransomware has the potential to cause significant damage to victims. By encrypting files and demanding a ransom for their decryption, the ransomware can disrupt operations, cause financial losses, and even lead to data breaches.
Some of the specific impacts of Kasseika ransomware include:
- Data loss: Victims may lose access to important files, such as documents, photos, and videos.
- Financial losses: Victims may have to pay the ransom to decrypt their files, or they may have to pay to recover their data from backups.
- Operational disruption: The ransomware can disrupt business operations, such as by preventing employees from accessing their files.
- Data breaches: If the ransomware encrypts sensitive data, it could lead to a data breach.
How to Protect Yourself from Kasseika Ransomware
There are a number of things that you can do to protect yourself from Kasseika ransomware and other ransomware threats:
- Keep your software up to date: This includes your operating system, antivirus software, and other applications. Outdated software is more likely to have security vulnerabilities that can be exploited by ransomware attackers.
- Use a strong antivirus program: A good antivirus program can help to detect and block ransomware attacks.
- Be careful about what emails you open and what links you click on: Ransomware is often spread through phishing emails. Don’t open emails or attachments from unknown senders, and be careful about clicking on links in emails, even if they appear to be from a trusted sender.
- Back up your files regularly: This is the most important thing you can do to protect yourself from ransomware. If your files are encrypted by ransomware, you can restore them from your backups without having to pay the ransom.
- Use a firewall: A firewall can help to block unauthorized access to your







