Key Highlights
- Getting to grips with how computer networks work and why the layout of these networks, or network topology, is key for linking devices together.
- With a look back at how computer networks have grown from their beginnings with ARPANET to today’s internet, we see the big part played by wide area networks and internet service providers.
- Talking about important moments in the history of networking, like when transmission media got better and when IEEE 802 standards came into play.
- Going over different ways to set up network topologies such as local area networks and metropolitan area networks.
- Looking at what’s good and bad about various network layouts while thinking about things like logical versus physical setups based on geographic location.
- Checking out what hardware makes up computer networks – think routers, switches, modems -and their role in keeping everything connected.
- With an eye on safety online, understanding why firewalls are crucial for protecting your data against unwanted access.
- Diving deep into how network protocols make sure computers can talk to each other properly focusing especially on TCP/IP protocol used in application layer
- Learning more about common types of communication rules between computers including HTTP HTTPS FTP which help us share information securely across web
- Breaking down IP addressing subnetting showing its importance within Network Layer Protocols ensuring every device has unique identifier online
- Wrapping it all up by going over main points again stressing just how essential knowing your way around computer Networks is nowadays
Mastering Computer Networks: A Comprehensive Guide
Computer networks play a big role in our everyday life, helping us to talk and share data with other devices. From surfing the web and sending emails to watching videos online, we need computer networks for pretty much everything. In this detailed guide, we’re going to explore all there is about computer networks – from the basic concept of a network to the more complex idea of a network of networks.
Getting a good grasp on how computer networks and their parts work is key for anyone who wants to get into tech. Once you understand computer networking well, you’ll know how to set up, adjust settings of network systems or fix them if something goes wrong. This guide isn’t just for students or IT experts; it’s also perfect if you’re just curious about how things like the internet function at its core. In this comprehensive guide, we will cover all aspects of computer network architecture, including hardware, software, transmission media, network topology, and communications protocols. Whether you are a beginner or an expert, this guide will help you master computer networks.
We’ll kick off by outlining what this guide will cover so you know what’s coming your way. After that, we’ll take a look back at how computer networks have evolved over time starting from ARPANET days up until today’s internet era. We’re going through important moments in network development too – think major leaps forward like improvements in transmission media and when IEEE 802 standards came along.
Following that path leads us into discussing different ways these networks can be arranged (network topologies), including their benefits and drawbacks alongside looking at essential networking gear such as routers, switches, modems, and other devices. Lastly, diving deep into protocols, a set of rules and standards that govern how data is transmitted over a network, ensuring smooth communication across the net. Wrapping things up, we will summarize why understanding computer networks is crucial in today’s world.
The Evolution of Computer Networks
The journey of computer networks has been pretty amazing, changing how we talk to each other and find information. It began with something called ARPANET in the 1960s, made by ARPA from the United States Department of Defense. This network linked up several research places and was the start of what we now know as the internet.
With time, bigger networks that could cover more ground, known as wide area networks (WANs), came into play. Internet service providers (ISPs) were super important because they gave people access to the internet, as well as cellular connectivity through wireless networks. Now, it’s hard to imagine life without the internet and cellular connectivity, as they connect so many devices all over the world.
From ARPANET to the Modern Internet
ARPANET was like the early version of today’s internet, making it possible for lots of computers to talk to each other and share stuff. Instead of sending all data at once, it broke things down into smaller bits called packets using something called packet switching. This way was totally different from how networks used to work before.
With time, ARPANET got bigger and turned into a wide area network (WAN), which meant it could connect places that were far apart. This change helped create the internet as we know it now. The introduction of certain rules for sending data over this network came with the Internet Protocol (IP). These rules made sure that when you send information across the internet, there’s a standard method for addressing where it goes, picking its path, and finally getting it delivered.
Key Milestones in Network Development
The journey of computer networks has hit some pretty big milestones that have changed how we talk to each other and share information. A huge step forward was making transmission media better. We went from old-school copper wires to fancy optical fibers, such as fiber optics, which let us send data at higher speeds and handle more info at once.
With the roll-out of IEEE 802 standards, things got even smoother in network development. These rules lay out what’s needed for network protocols and techs so everything can work together nicely. Take IEEE 802.11, or Wi-Fi as most of us call it; this was a game-changer because it meant you could connect to the internet wirelessly through a wireless router without being tied down by cables.
Thanks to these advancements, our networks are now faster, can be relied on more than ever before, and can grow with our needs – making it easier for all of us to chat up a storm online or dig up whatever info we need.
Understanding Network Topologies
Network topology is all about how the parts of a network, like computers and connections, are set up. It’s key for figuring out how to put together, use, and look after computer networks. This setup affects how data moves around in the network.
- With local area networks (LANs), devices get connected over a small space – think an office building.
- On the other hand, metropolitan area networks (MANs) link devices over bigger places such as cities.
Each way of setting things up has its own pros and cons based on what you need from your network.
Common Network Configurations

Talking about setting up networks, there are a few usual ways people do this for both small and big networks. These methods outline how gadgets link up and the path data takes in the network.
For smaller, local networks:
- With Bus topology, imagine all devices lined up with a main cable connecting them. This main cable is known as the bus. When information needs to get somewhere, it travels along this bus until it finds its destination.
- Star topology has each device connected to a central point like spokes on a wheel. This center could be either a hub or switch where all info passes through, making sure messages get from one gadget to another.
- In Ring topology, think of your devices forming a circle where each one connects to two others creating a loop. Information moves in just one direction around this loop till it gets where it’s supposed to go.
Besides these setups, wireless devices like laptops and phones can join onto these local networks without wires using something called access points which makes moving around easy while staying connected.
Pros and Cons of Different Topologies
When it comes to setting up a network, the layout you pick is pretty important. This choice should be based on what the network needs to do, how big it is, and other specific things that are needed.
Let’s talk about some of the good and bad points of different layouts:
- For Bus topology: On the plus side: It’s straightforward and doesn’t cost much if your network isn’t too big. But on the downside: If one part goes wrong, everything can stop working. Also, it can’t handle lots of data or grow very easily.
- With Star topology: The good stuff includes being easier to look after and fix problems with. It works better as you add more devices and keeps each device separate from others. However, all devices depend on one central point which could be a problem if that fails. And because you need extra equipment like hubs or switches, costs go up.
- As for Ring topology: Its advantages are that every device gets an equal chance at sending data transmission, making sure there’s no jamming in communication lines while keeping information moving smoothly. The drawbacks? It’s tough figuring out where issues lie when they pop up; if just one gadget stops working right; it might affect everyone else connected in this circle—not forgetting its growth limitations too.
Choosing depends heavily on whether having backup options (redundancy), room for expansion (scalability), or performance matters most for your setup.
Networking Hardware Explained
Networking hardware is all about the physical bits and pieces that help computers connect with each other, share data, and keep everything running smoothly. It’s like the backbone of a computer network.
Here are some key parts:
- Routers: Think of routers as traffic cops for networks. They link different networks together and figure out the best way to send data from one place to another by looking at network traffic.
- Switches: These are like organizers inside a single network. They make sure messages get sent to the right computer by using something called a MAC address.
- Modems: Modems are translators between digital and analog signals so that devices can use telephone lines or similar paths to hop onto the internet or other networks.
Together, these components ensure we can chat, stream videos, or work online without hiccups thanks to efficient data transmission over various channels including telephone lines.
Routers, Switches, and Modems



Routers, switches, and modems are the backbone of any network. They make sure our devices talk to each other smoothly and that our data gets where it needs to go without a hitch.
- With routers, we’re looking at the bosses of directing traffic on the internet highway. They connect different networks together like bridges between islands. By checking out network traffic, they pick the best routes for sending information, so it arrives quickly and safely at its destination. Routers rely on something called Internet Protocol (IP) to get this job done right.
- Then there are switches. Think of them as managers inside an office building who ensure everyone’s messages get delivered straight to their desk without getting lost in the hallway shuffle. Switches keep things orderly by using access control with Media Access Control (MAC) addresses, so data packets find their way directly to the correct device within a network.
- Lastly, modems act like translators between digital devices and old-school telephone lines allowing us all onto the vast world wide web through dial-up connections or broadband services alike! Modem stands for “modulator-demodulator,” which means they turn digital signals from your computer into analog ones that can travel over phone lines then change them back again once they reach their target.
Together these gadgets work tirelessly behind scenes ensuring seamless connectivity across various platforms whether you’re streaming videos online or just browsing websites—all thanks to efficient handling of data transmission among networks.
The Role of Firewalls in Network Security

In our world today, where everything is connected, keeping networks safe is super important. Firewalls are key to this because they help keep out unwanted access and harmful activities that could threaten the security of these networks.
A firewall works like a guard who checks all the data coming in and going out of a network against some set rules. It’s there to make sure only good data gets through while stopping any bad or fishy data from entering or leaving.
To do their job well, firewalls use different methods like checking who’s trying to enter (access control), examining each piece of data closely (packet filtering), looking at the state of connections (stateful inspection), and preventing attacks before they happen with intrusion prevention systems. Depending on what a network needs, firewalls can be physical gadgets you plug in or just programs you run on your computer.
By using firewalls, companies can keep their networks off-limits from intruders, viruses, and other dangers. This way they protect all the important information stored inside these networks while making sure everything runs smoothly without any threats messing things up.
Diving into Network Protocols
Network protocols act like a bunch of guidelines and steps that help in sending and getting data across a network. They make sure data moves smoothly and efficiently from one device to another within the network.
Among these, the TCP/IP protocol suite is super popular for talking over networks based on IP, like the internet. This suite includes different layers: there’s an application layer, transport layer, internet layer, and network interface layer.
At the application layer, you’ll find protocols such as HTTP, HTTPS FTP, and SMTP which lay out how apps should chat with each other and swap information across the netowrok. These are what let us browse websites, file transfer, email communication
For those who manage networks or work in IT, knowing about these protocols is key to keeping things running without hitches
TCP/IP and Its Functions
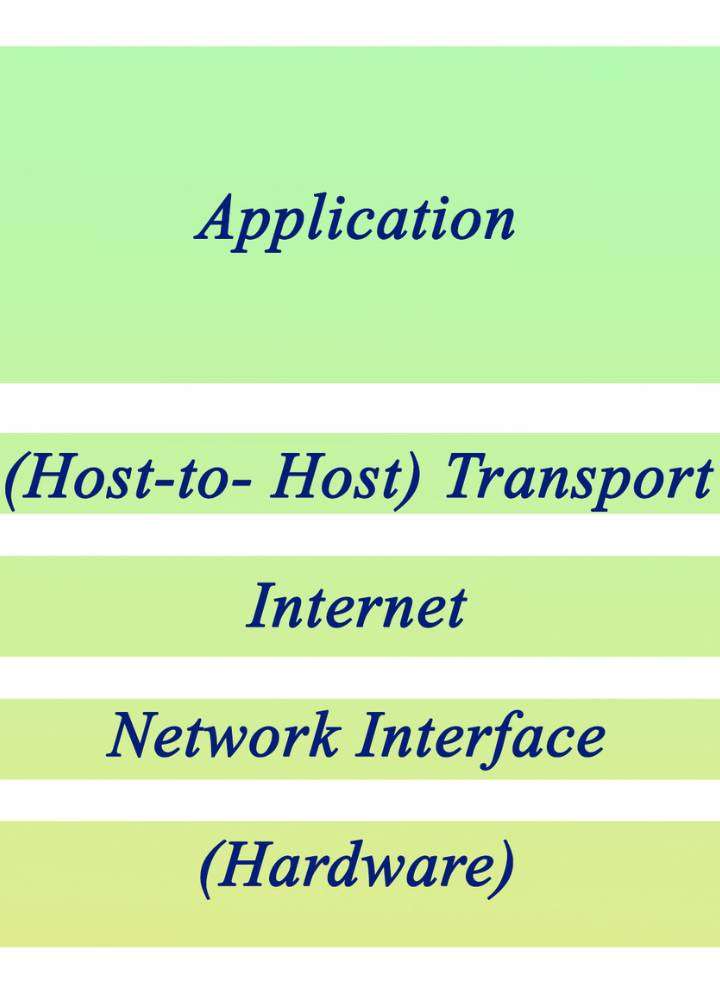
The TCP/IP protocol suite is like the backbone of how we talk to each other on the internet. It’s made up of a bunch of rules that make sure data gets from one place to another smoothly and reliably over networks that use IP.
Let’s break it down into its four main parts:
- At the application layer, you find all sorts of protocols and services designed for specific apps used by devices connected online. For instance, when you’re browsing websites, sending emails or transferring files, protocols like HTTP, FTP, and SMTP come into play here.
- With the transport layer comes the job of making sure messages get where they’re supposed to go without messing up along the way. The Transmission Control Protocol (TCP) lives here; it checks for errors and manages traffic, so everything flows nicely without clogging up. Then there’s UDP – User Datagram Protocol – which doesn’t worry much about checking if everything arrived in order but keeps things moving fast even though some bits might drop.
- Over at the internet layer is where packets are sent off across various networks with guidance from Internet Protocol (IP). This part makes sure those packets reach their correct destination among all possible paths available.
- Lastly, we have network interface layers dealing directly with getting data packets out through physical means – think cables or airwaves – covering both hardware aspects and certain software processes needed at this very basic level.
By having these layers work together as a team within TCP/IP protocol suite allows different gadgets to chat away freely using IP-based networks including what powers our web surfing sessions today such as application layer functions or ensuring smooth delivery via transport mechanisms guided by none other than our friend Internet Protocol.
Understanding HTTP, HTTPS, and FTP
HTTP, HTTPS, and FTP are key tools that help move different kinds of data across computer networks.
- With HTTP (Hypertext Transfer Protocol), the web comes to life. It’s what lets your browser fetch and show you websites from servers. This happens on the application layer of how computers talk to each other over the internet, with a setup where your browser asks for info from a server which then sends it back.
- For a safer online experience, there’s HTTPS (Hypertext Transfer Protocol Secure). It takes everything good about HTTP and locks it down with encryption using SSL or TLS protocols. This means when you’re sending sensitive info over the web, like passwords or credit card numbers, they’re protected by this secure connection between your browser and the website’s server.
- When it comes to moving files around on a network, FTP (File Transfer Protocol) is what you need. Whether uploading or downloading files from remote servers or managing them online; FTP has got you covered. Like HTTP but specifically for file transfers; this too works based on asking for something from another computer over an application layer protocol suite known as TCP/IP.
For anyone building websites, running networks or just surfing the web – knowing these protocols helps keep things smooth and safe during data transmission across networks.
IP Addressing and Subnetting
In the world of computer networking, knowing how IP addressing and subnetting work is key for devices to talk to each other and share data over networks.
An IP address acts like a unique tag for every device on a network, made up of four groups of numbers split by dots, like 192.168.0.1 for example. There are two main flavors: IPv4 and IPv6. The older version, IPv4 uses 32 bits creating addresses that look familiar to most people while the newer IPv6 stretches out to 128 bits giving us way more addresses as more gadgets hook up online.
With subnetting, we chop up bigger networks into smaller chunks called subnets which helps in making better use of our pool of IP addresses besides boosting how well our networks run and keeping them secure too. It’s all about organizing things so you can handle where IPs go with ease and set your network’s structure just right.
For those who dive deep into setting up or fixing networks—like network admins or IT pros—it’s crucial they get these concepts down pat.
Basics of IP Addressing
Every device that connects to the internet gets a special number called an IP address, which is like its home address on the network. This helps devices talk to each other. There are two kinds of these addresses: IPv4 and IPv6.
With IPv4, you get an address made up of four groups of numbers split by dots, something like 192.168.0.1. Each group has 8 bits making it a total of 32 bits for the whole thing. But because there’s only so many combinations we can make with this system, and since more and more gadgets are hopping online every day, we came up with another version called IPv6.
IPv6 uses letters and numbers in eight groups separated by colons (for example: 2001:0db8:85a3:0000:0000:8a2e:0370:7334). It gives us way more possible addresses so lots more devices can join in without running out.
Then there’s something else cool – domain names like google.com make it easier for us humans since remembering all those numbers would be tough! These friendly names get turned into IP addresses through something known as DNS so our browsers know where to take us when we type them in or click on a link.
Subnetting Techniques and Practices
Subnetting is like cutting a big network into smaller pieces called subnets. It’s a smart way to hand out IP addresses and keep the network organized.
With subnetting, you can make little networks inside a bigger one. Each of these small networks gets its own special address and rules for what IP addresses it can use. This setup helps devices in the same subnet talk to each other more easily.
By breaking down a network this way, companies can make their networks run better, be safer from attacks, and grow without trouble. Subnetting makes sure not too many IPs are wasted by making lots of smaller groups that are easier to handle.
There are different ways to do subnetting, like using Variable Length Subnet Masking (VLSM) or Classless Inter-Domain Routing (CIDR). These methods give people more choices on how they split up their network space.
In short, subnetting plays a big role in setting up and running networks well. It lets us use IP addresses wisely while keeping everything tidy and working smoothly within logical networks.
The OSI and TCP/IP Models
When we talk about how computers send messages to each other over the internet, there are two main ways people understand it: through the OSI model and the TCP/IP model.
With seven layers – Physical, Data Link, Network, Transport, Session, Presentation, and Application – the OSI model breaks down everything that happens when data moves from one place to another. Each layer deals with a different part of this process.
On another note, is the TCP/IP model which has four parts: Network Interface, Internet (where our keyword “internet protocol” comes into play), Transport and Application. This way of looking at network communication is what most of today’s internet uses as its base.
Both these models help folks who manage networks get why data gets sent smoothly or sometimes doesn’t make it at all by showing them what goes on at every step along this journey.
Breaking Down the OSI Model Layer by Layer
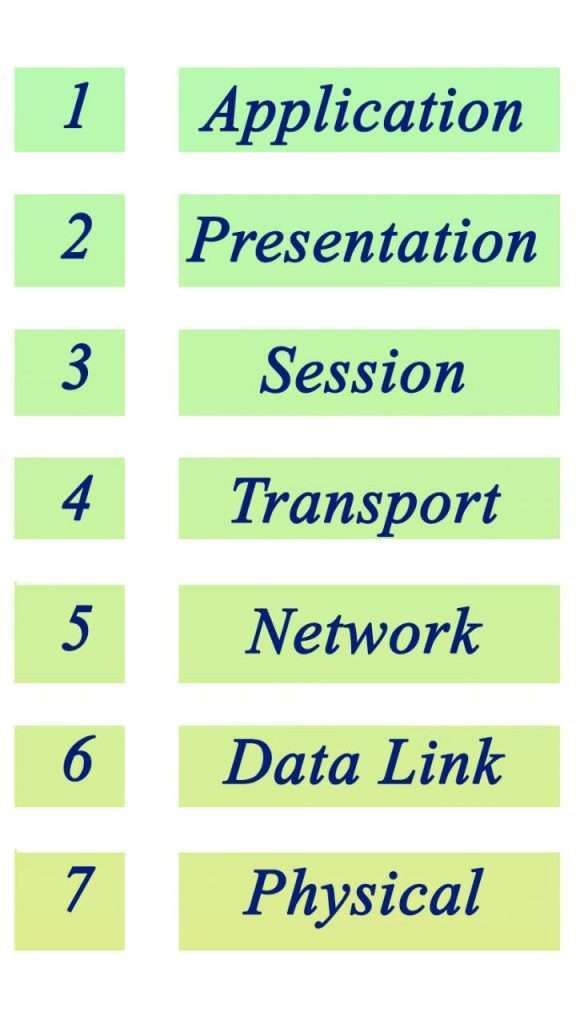
In the world of networking, there’s a structure called the OSI model that breaks down network communication into seven distinct layers. Each layer has its own job to make sure data moves smoothly from one point to another.
- With the physical layer, we’re talking about getting those bits of data across through cables or wireless signals. It’s all about making a connection and sending raw info.
- Moving up, at the data link layer, it’s key for making sure messages get between devices without messing up. This is where data gets packaged nicely and checked for any errors before it goes on its journey.
- The network layer takes care of directions; think of it as your GPS for navigating packets across various networks using IP addresses so they know where they’re going.
- Then comes the transportation layer, which makes sure messages are delivered reliably and in order. If something goes wrong, like an error or if things start piling up too fast, this is what keeps everything running smooth.
- At the session level, we have our fifth player: The session later ensures conversations can start, go on without hitches, and end properly when done exchanging information.
- For ensuring everyone speaks a common language regardless of their system setup,the presentation later steps in. It translates different formats so whatever you send arrives understandable no matter what kind software is being used at other end
The final piece application allows users interact with services over internet whether emailing, browsing web transferring files, it connects people stuff need online
Each step here plays crucial role keeping digital communications clear trouble-free. Knowing how these pieces fit together helps solve problems and keep networks happy
TCP/IP Model vs. OSI Model
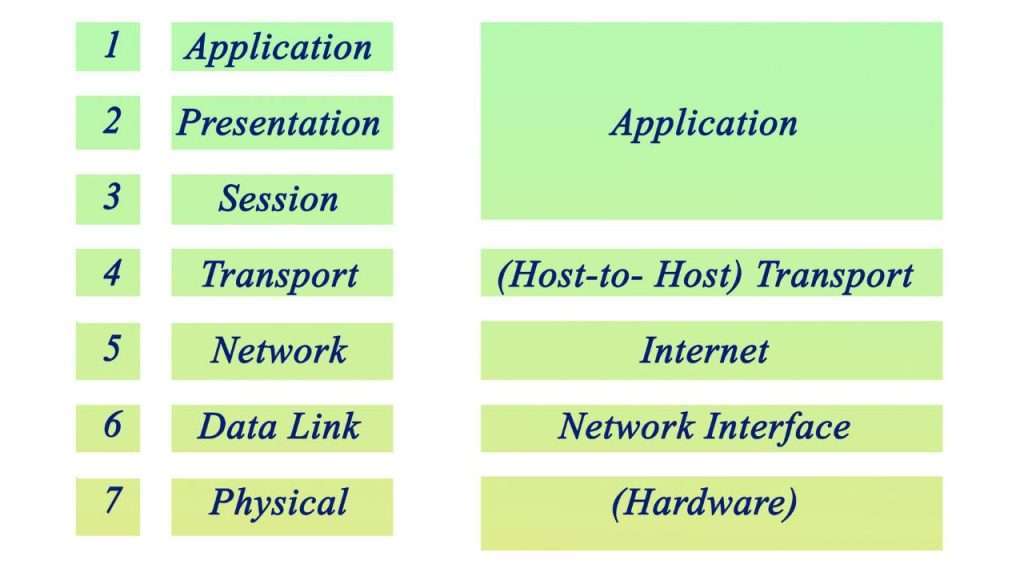
When we talk about how networks communicate, two main models come up: the TCP/IP model and the OSI model. They’re both used to explain how network protocols work, but they do have their differences.
At its core, the TCP/IP model is what keeps the internet running today. It’s made up of four layers: Network Interface, Internet, Transport, and Application. This setup focuses on just what’s needed for online communication to happen smoothly.
In contrast with this simplicity stands the OSI model which breaks things down into seven layers: Physical, Data Link, Network, Transport, Session, Presentation, Application.
This approach gives a fuller picture of all that goes into network communications.
Even though these models are different in structure and detail level each plays an important role for those who make sure our networks run without a hitch The go-to choice often is TCP/IP because it directly applies to real-world networking Yet understanding OSI can really help get why networks operate as they do
Emerging Technologies in Networking
Emerging technologies are changing how we communicate and connect. At the forefront of this change, we have Software-Defined Networking (SDN), the Internet of Things (IoT), and cloud computing.
With SDN, there’s a clear split between where network decisions are made and where data gets sent. This setup lets one central point control everything about the network, making it easier to manage, scale up or down as needed, and automate tasks.
When talking about IoT, think of all sorts of gadgets—like your fridge or car—talking to each other over the internet. They share information that helps them work smarter together.
Cloud computing is like having a giant computer online that anyone can use when they need extra power for their apps or services. It’s great because you only pay for what you use and can easily get more resources without buying expensive hardware.
These new techs are not just cool; they’re reshaping industries by making networks smarter, more flexible, and better connected than ever before.
Software-Defined Networking (SDN)

Software-Defined Networking, or SDN for short, is a new way of setting up networks that makes it easier to control and change how data moves around. Instead of having the parts that decide where data goes stuck together with the parts that actually move the data, SDN keeps them separate. This setup lets one central point manage everything.
With old-style networks, mixing these two functions made it tough to handle and tweak network devices. By separating them through SDN allows for all traffic management and resources across the network from one spot.
Through a software controller, SDN can tell network devices what to do so they can adjust how they send information based on what an application needs at any moment. This ability means things can get done quicker; managing the network becomes less complicated and grows more easily.
On top of this flexibility in handling network traffic, automation comes into play with SDN making routine network administration jobs less hands-on which boosts efficiency big time It even makes possible creating virtual sections within a physical network tailored specifically for certain apps’ demands
All in all, SDN is changing game by helping businesses keep up better as their networking needs evolve becoming smarter about dealing with changes fast
The Impact of IoT on Networks

The Internet of Things, or IoT for short, is making big changes by hooking up everyday items and gadgets to the internet. This creates a huge web of devices that can talk to each other, share data, and even make sense of it all.
With more gadgets getting connected thanks to IoT, networks are really feeling the pressure. They’re dealing with more data traffic than ever before and need to be able not just handle this increase but also stay flexible and safe from threats.
Because these IoT devices are always sending out tons of information, networks have their work cut out for them. Services related to networks like storing data, processing it quickly, and analyzing it play a key role in making sure we get the most out of what IoT has to offer.
When talking about keeping everything secure, it’s super important especially with so many devices being linked together now. This means there’s more chance for security issues which nobody wants. That’s why having strong network security measures such as access control, is crucial. It helps keep our connected things safe from harm.
In summary, the rise in popularity of IoT is pushing for better and more advanced network infrastructure, services, and security measures to deal with the increasing number of connected devices and their data needs.
Cybersecurity Fundamentals

Cybersecurity plays a key role in keeping our networks safe from various security threats and weaknesses. It’s all about the steps, actions, and technology we use to protect our networks, gadgets, and information from being accessed or attacked by someone who shouldn’t.
With network security, the focus is on protecting the structure of our networks. This means making sure that data stays confidential, unchanged unless necessary (integrity), and available when needed. To do this effectively involves using tools like firewalls to block unwanted access; systems that detect intruders trying to get into our network; and encryption methods which scramble data so only authorized people can read it.
Educating those who use these networks is also part of cybersecurity. Teaching them how important strong passwords are; reminding them to update their software regularly helps keep potential attackers at bay; plus raising awareness about what kinds of security risks exist out there today makes everyone safer.
Organizations must have plans ready for responding if something does go wrong (incident response plans) while constantly checking their defenses against attacks (monitoring) so they can fix any weak spots before trouble starts.
By sticking with basic principles of cybersecurity organizations stand a better chance at defending themselves against attempts to break into their systems or steal sensitive info—reducing not just chances for unauthorized entry but also lessening impacts should breaches occur involving network security or other security threats.
Common Network Threats and Vulnerabilities
With network security being a big deal, it’s super important to know about the dangers and weak spots that can hurt our networks. This knowledge is key to keeping everything safe.
For starters, there are all sorts of nasty software out there like viruses, worms, and ransomware. These bad guys can mess up your devices and steal your data. Then you’ve got phishing attacks where tricksters make you give up personal info without realizing it.
On top of these threats, we have vulnerabilities which are basically chinks in our armor. They might come from not setting things up right on the network or using old software that doesn’t cut it anymore. Weak passwords or not dividing the network into secure zones can also invite troublemakers in.
To fight off these issues, putting strong defenses in place is crucial—think firewalls to keep invaders out, systems that spot intruders trying to sneak past us unnoticed, encryption for scrambling data so prying eyes can’t read it easily, and access controls for managing user permissions. With the constant addition of new devices and changes in user access, it is important to regularly check for any weaknesses and update systems as needed. Automating wherever possible can also help in staying on top of security threats.
By getting a grip on common security threats and fixing those gaps where attackers could get through organizations stand a better chance at safeguarding their networks against unwanted surprises.
Best Practices for Network Security
To keep networks safe from security threats and make sure data and resources stay confidential, secure, and available, it’s crucial to follow the best methods for network security.
- With strong access controls in place: By setting up tough passwords, using multi-factor authentication, and assigning roles-based access limits can help prevent unauthorized entry into the network.
- By keeping network devices updated: It’s important to regularly check that all your network tools and software are current with the latest fixes for known weak spots.
- Through encrypting sensitive information: Protecting private data while it’s being sent or stored by using encryption means even if someone gets their hands on it, they won’t be able to understand it without authorization.
- By breaking down the network into smaller parts: Creating separate segments within your larger network can help control a potential breach better so that not everything is affected at once.
- In training staff about staying safe online: Teaching people who use your networks how to spot risky emails or links and telling them how important it is to report any odd activities right away helps everyone stay safer.
Adopting these strategies will significantly bolster an organization’s defense against unwanted intrusions into its systems.
Conclusion
To get really good at computer networks, it’s important to know how they’ve changed over time, the different layouts they can have, the physical parts involved, and the rules that help them work smoothly. You should also look into how IP addresses are assigned and divided up (that’s subnetting), along with basic stuff about keeping a network safe. It’s crucial to keep an eye on common risks and weak spots while learning the best ways to protect networks. Get ready for new tech like SDN (Software-Defined Networking) and understand how things like IoT (Internet of Things) are changing networks as we know them. If you’ve got questions, don’t hesitate to ask – there’s always more to learn! And if staying in-the-know about all this sounds good to you, think about signing up for updates so you never miss out on what’s new in network security.
Frequently Asked Questions
What are the different types of computer networks?
Computer networks come in several types, such as LAN (Local Area Network), WAN (Wide Area Network), WLAN (Wireless Local Area Network), MAN (Metropolitan Area Network), and CAN (Campus Area Network). Each serves a specific purpose and has varying geographical coverage and connection capabilities.
What Is the Difference Between a Router and a Switch?
A router and a switch are important gadgets in the world of networking, but they do different jobs. With a router, you can link up various networks and move data from one to another. On the other hand, a switch connects devices within the same network and helps manage how data traffic flows between them.
What are the key components of a computer network?
In a computer network, there are some main parts that make everything work. First off, we have the network architecture. This is like the blueprint of the whole setup, showing how it’s all put together. Then, there are central servers in charge of looking after all the resources on the network. We also have what’s called network nodes; these help different devices talk to each other. And lastly, for sending data back and forth, we use something known as transmission media – this could be cables or even wireless signals flying through the air.
What are some common networking protocols and their purposes?
In the world of computers, there are some common rules that help our devices talk to each other. One of these is TCP/IP, which makes sure data gets where it’s going safely and in order. Another important one is HTTP, which lets web servers and browsers communicate with each other. These sets of rules are called protocols, and they’re crucial for sending and receiving information across networks.







