Networking stands as the backbone of modern communication, orchestrating the seamless exchange of data across vast distances and diverse devices. At its core lies a complex ecosystem of protocols, layers, and encapsulation techniques meticulously designed to govern and optimize data transmission. In this extensive and in-depth exploration of protocols, we embark on a journey to dissect the intricacies of networking protocols, delve into the architecture of protocol layers, unravel the ISO/OSI model, and scrutinize the mechanisms of encapsulation. Through detailed analysis and practical examples, we aim to equip readers with a comprehensive understanding of these fundamental components that underpin the digital infrastructure of our interconnected world.
Protocols: Orchestrating Communication

Protocols serve as the guiding principles that dictate communication between networked devices, defining the rules and conventions governing data transmission and reception.
Packets: The Currency of Data Transmission

Packets represent the fundamental units of data transmission in networking, encapsulating both the payload and essential header information necessary for routing and delivery.
Anatomy of Network Packets Network packets encapsulate data along with essential control information, enabling its transmission across networks. The anatomy of a network packet consists of distinct components, each serving a specific purpose in the data transmission process:
Header
The header serves as the metadata section of the packet, containing vital information required for routing, error detection, and protocol handling. Key fields typically found in packet headers include:
- Source and Destination Addresses: Identify the sender and recipient of the packet.
- Protocol Type: Specifies the protocol encapsulated within the packet (e.g., TCP, UDP, ICMP).
- Packet Length: Indicates the total size of the packet, including both the header and payload.
- Time to Live (TTL): Specifies the maximum number of router hops the packet can traverse before being discarded.
- Checksum: Provides error detection capabilities to ensure data integrity during transmission.
- Fragmentation Information: Facilitates packet fragmentation and reassembly for efficient transmission across networks.
Payload
The payload constitutes the actual data being transmitted within the packet. It can vary in size and content depending on the application and protocol being used. Common examples of payload data include:
- Application Data: Such as text, images, audio, video, or any other form of digital content.
- Control Information: Commands, requests, or responses exchanged between networked devices.
- Protocol-specific Data: Information relevant to the specific protocol being utilized, such as TCP segments or UDP datagrams.
Trailer (Optional)
In some cases, a trailer section may be appended to the packet, containing additional control information or error detection codes. While not always present, trailers can enhance the reliability and integrity of data transmission.
Functionality of Network Packets
Network packets play a pivotal role in facilitating communication between networked devices by enabling the efficient exchange of data. The functionality of network packets encompasses several critical aspects:
Routing
Packets contain routing information, including source and destination addresses, enabling routers to determine the optimal path for packet delivery across networks. As packets traverse the network infrastructure, routers examine their headers to make forwarding decisions based on routing tables and network policies.
Error Detection and Correction
Packets incorporate checksums and other error detection mechanisms to ensure data integrity during transmission. Upon receiving a packet, the recipient device verifies the integrity of the data by recalculating the checksum and comparing it to the value included in the packet header. If discrepancies are detected, error correction mechanisms may be invoked to retransmit or repair the corrupted data.
Fragmentation and Reassembly
In scenarios where the packet size exceeds the maximum transmission unit (MTU) of a network link, packets may undergo fragmentation, where they are divided into smaller segments for transmission. Upon reaching their destination, fragmented packets are reassembled into their original form based on the fragmentation information included in their headers.
Protocol Handling
Packets encapsulate data according to specific networking protocols, such as TCP/IP, UDP, ICMP, or IPsec. Each protocol defines its own packet format, header fields, and transmission semantics, influencing how packets are processed and routed within the network.
Role of Network Packets in Data Transmission
Network packets serve as the conduits through which data is transmitted and received across networks, enabling seamless communication between devices. The role of network packets in data transmission encompasses several key aspects:
Interoperability
By adhering to standardized packet formats and protocols, network packets ensure interoperability between diverse networking devices and systems. Regardless of the underlying hardware or software, devices can exchange data reliably using a common packet structure and protocol stack.
Scalability
Network packets facilitate scalable communication architectures by enabling the efficient transmission of data across networks of varying sizes and complexities. As network traffic grows and evolves, packets can be routed dynamically to adapt to changing network conditions and demands.
Security
Network packets play a crucial role in network security by incorporating mechanisms for encryption, authentication, and access control. By encapsulating data within secure packet structures, sensitive information can be transmitted securely across untrusted networks, safeguarding against unauthorized access and interception.
Performance Optimization
Through techniques such as packet prioritization, Quality of Service (QoS) routing, and traffic shaping, network packets enable the optimization of network performance and resource utilization. By prioritizing critical traffic and allocating bandwidth efficiently, packets ensure timely delivery of data and mitigate network congestion.
Dissecting the IP Header: A Closer Look

The IP header is positioned between the data link layer and the transport layer in the OSI model, encapsulating the data payload and providing the necessary information for routers and switches to route the packet to its destination. Let’s break down the structure of the IP header:
Version (4 bits)
The Version field indicates the version of the IP protocol being used. In IPv4, the most widely deployed version, this field is set to 4.
Header Length (4 bits)
The Header Length field specifies the length of the IP header in 32-bit words. Since the header length is variable due to optional fields, this value helps devices determine the start of the data payload.
Type of Service (8 bits)
The Type of Service (TOS) field is used to prioritize packets based on different characteristics, such as delay, throughput, reliability, and cost. It allows for Quality of Service (QoS) differentiation in network traffic.
Total Length (16 bits)
The Total Length field indicates the total size of the IP packet, including both the header and the data payload. It ranges from 20 to 65,535 bytes.
Identification (16 bits)
The Identification field provides a unique identifier for the IP packet, assisting in the reassembly of fragmented packets at the destination.
Flags (3 bits) and Fragment Offset (13 bits)
The Flags and Fragment Offset fields work together to manage packet fragmentation. The Flags field includes three bits: Reserved, Don’t Fragment (DF), and More Fragments (MF). The Fragment Offset specifies the position of the fragment in the original unfragmented packet.
Time to Live (TTL – 8 bits)
The Time to Live field represents the maximum number of hops a packet can take before being discarded. It is decremented at each router hop to prevent packets from circulating indefinitely.
Protocol (8 bits)
The Protocol field identifies the protocol used in the data portion of the packet. Common values include 6 for TCP, 17 for UDP, and 1 for ICMP.
Header Checksum (16 bits)
The Header Checksum field provides error-checking for the IP header. It is recalculated at each hop to verify the integrity of the header.
Source IP Address (32 bits) and Destination IP Address (32 bits):
The Source and Destination IP Address fields specify the sender and recipient of the IP packet, respectively.
IP Header Example
To better illustrate the structure of the IP header, let’s examine a hypothetical example:
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|Version| HLen | TOS | Total Length | Identification |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Flags | Fragment Offset | Time to Live (TTL) | Protocol |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Header Checksum | Source IP Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Destination IP Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
In this example:
- Version: 4 (IPv4)
- Header Length (HLen): 5 (indicating 5 * 32-bit words, or 20 bytes)
- Type of Service (TOS): 0 (default)
- Total Length: Variable, based on the size of the data payload
- Identification: Unique identifier for the packet
- Flags: Reserved (0), Don’t Fragment (DF), More Fragments (MF)
- Fragment Offset: Position of the fragment in the original packet
- Time to Live (TTL): Variable, starting from a predetermined value (e.g., 64 or 128)
- Protocol: Specifies the encapsulated protocol (e.g., 6 for TCP, 17 for UDP)
- Header Checksum: Calculated checksum for error detection
- Source IP Address: IP address of the sender
- Destination IP Address: IP address of the recipient
Significance of IP Header Fields
Each field in the IP header serves a specific purpose, contributing to the efficient and reliable transmission of data across networks. Here’s a detailed look at the significance of key IP header fields:
- Version and Header Length: These fields establish the version of the IP protocol and the length of the header, allowing devices to interpret the structure of the packet.
- Type of Service: The TOS field enables Quality of Service (QoS) differentiation, allowing for prioritization of packets based on specific characteristics.
- Total Length: The Total Length field specifies the size of the entire packet, aiding in proper packet processing and routing.
- Identification, Flags, and Fragment Offset: These fields manage packet fragmentation, ensuring efficient transmission and reassembly of fragmented packets at the destination.
- Time to Live (TTL): The TTL field prevents packets from circulating indefinitely, promoting efficient routing and preventing network congestion.
- Protocol: The Protocol field identifies the encapsulated protocol, enabling devices to forward packets to the appropriate higher-layer protocol for further processing.
- Header Checksum: The Header Checksum field provides error-checking for the IP header, ensuring the integrity of the header information during transit.
- Source and Destination IP Address: These fields specify the source and destination IP addresses, essential for routing and delivering packets to the intended recipients.
Protocol Layers: Hierarchical Organization of Networking Functions
Protocol layers represent a systematic approach to networking design, where different functionalities are segregated into discrete layers, each building upon the services provided by the layer beneath it. The concept of protocol layers is epitomized by the OSI (Open Systems Interconnection) model and the TCP/IP (Transmission Control Protocol/Internet Protocol) suite, two prominent frameworks used to conceptualize and implement network architectures.
The OSI Model: A Blueprint for Layered Networking
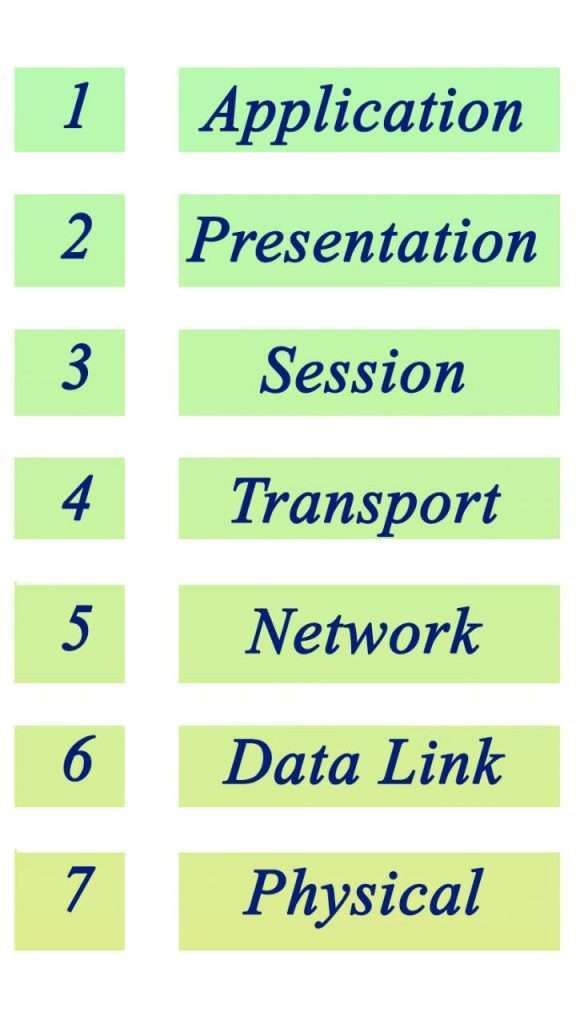
The OSI model, developed by the International Organization for Standardization (ISO), defines a conceptual framework comprising seven distinct layers. Each layer encapsulates specific functionalities and interfaces with adjacent layers through well-defined protocols and service interfaces. The OSI model serves as a blueprint for designing interoperable and scalable network systems, facilitating standardized communication between diverse devices and platforms.
Physical Layer
The physical layer represents the lowest level of the OSI model, responsible for transmitting raw binary data over physical media such as copper wires, fiber-optic cables, and wireless channels. It defines attributes such as voltage levels, signaling methods, and data rates, shaping the fundamental aspects of network connectivity.
Data Link Layer
Sitting atop the physical layer, the data link layer ensures reliable communication between directly connected devices. It handles tasks such as framing, error detection, and media access control (MAC), facilitating the efficient transmission of data frames across local network segments.
Network Layer
The network layer facilitates end-to-end packet delivery and routing across interconnected networks. It is responsible for logical addressing, routing, and traffic management, enabling devices to communicate across disparate network segments using IP (Internet Protocol) addresses.
Transport Layer
The transport layer ensures reliable and efficient data transfer between end systems. It provides mechanisms for segmentation, error recovery, congestion control, and end-to-end flow control, guaranteeing the integrity and reliability of data transmission through protocols like TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
Session Layer
The session layer establishes, maintains, and terminates communication sessions between network entities. It handles functions such as session initialization, synchronization, and data exchange, enabling applications to establish and manage long-lived connections.
Presentation Layer
Focused on data representation and translation, the presentation layer standardizes data formats, encoding schemes, and encryption methods. It ensures compatibility between heterogeneous systems by facilitating the conversion and interpretation of data across different platforms.
Application Layer
At the highest level, the application layer provides network services and interfaces for user applications. It encompasses protocols such as HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and DNS (Domain Name System), enabling the development of distributed applications and services.
The TCP/IP Protocol Suite
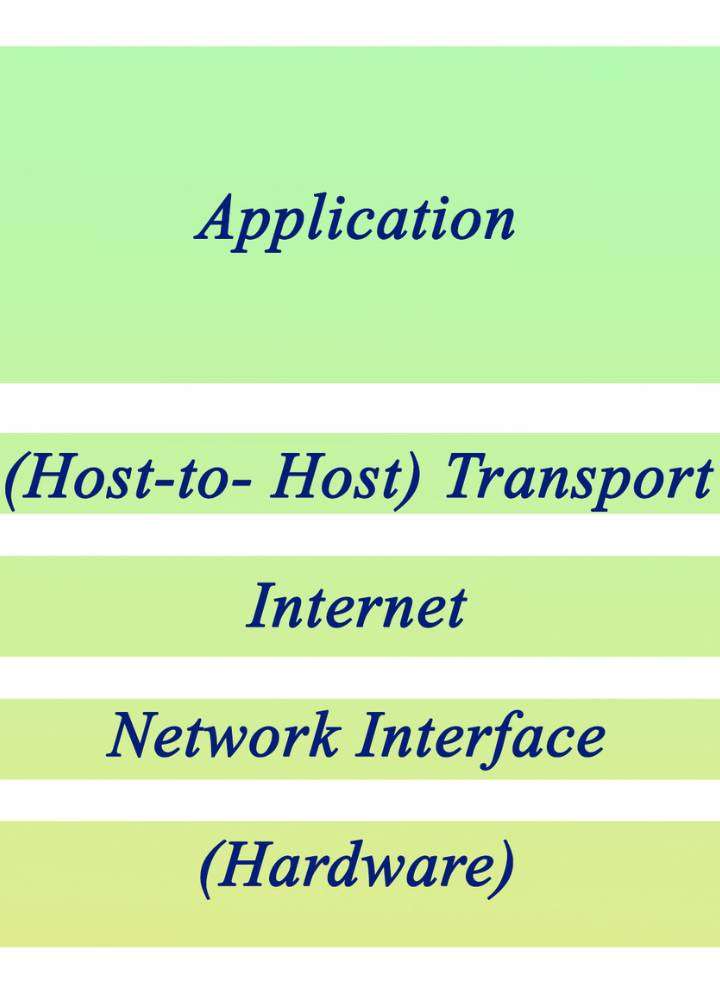
Practical Implementation of Layered Networking While the OSI model provides a conceptual framework for layered networking, the TCP/IP protocol suite serves as a practical implementation of these principles. The TCP/IP stack consists of four primary layers, each serving specific functions in the transmission and reception of data packets across the Internet.
Link Layer
The link layer in the TCP/IP stack corresponds to the combination of the OSI data link and physical layers. It encompasses protocols such as Ethernet, Wi-Fi, and PPP (Point-to-Point Protocol), defining the mechanisms for transmitting data frames over local and wide area networks.
Internet Layer
Equivalent to the OSI network layer, the Internet layer is responsible for addressing, routing, and packet forwarding across interconnected networks. It utilizes the IP protocol to encapsulate data packets and facilitate end-to-end communication between devices.
Transport Layer
The transport layer in the TCP/IP stack mirrors the functionality of the OSI transport layer, providing reliable and connection-oriented data transmission services. TCP and UDP are the two primary protocols operating at this layer, offering mechanisms for segmentation, error recovery, and flow control.
Application Layer
The application layer encompasses a wide range of protocols and services that facilitate user-level communication and interaction. It includes protocols such as HTTP, FTP, SMTP, DNS, and SNMP (Simple Network Management Protocol), enabling applications to access network resources and exchange data with remote servers.
Real-World Examples and Applications
The concept of protocol layers finds widespread application across various networking technologies and industries. Some notable examples include:
- Ethernet: Ethernet, a widely used LAN (Local Area Network) technology, operates at the data link layer of the OSI model. It employs protocols such as IEEE 802.3 to define the framing, addressing, and collision detection mechanisms used to transmit data over Ethernet networks.
- TCP/IP Networking: The TCP/IP protocol suite forms the basis of Internet communication, providing the underlying protocols and standards that govern data transmission across the global network. TCP and IP operate at the transport and internet layers, respectively, enabling reliable and scalable communication between devices worldwide.
- Wireless Communication: In wireless communication systems such as Wi-Fi and cellular networks, protocol layers play a crucial role in managing radio frequency transmission, signal modulation, and packet routing. Protocols like IEEE 802.11 govern Wi-Fi communication, while cellular networks rely on standards such as GSM (Global System for Mobile Communications) and LTE (Long-Term Evolution) for wireless connectivity.
ISO/OSI Model: Blueprint for Interoperability and Scalability
The ISO/OSI model delineates networking protocols and architectures into seven distinct layers, providing a standardized framework for designing interoperable and scalable network systems.
- Layer 1: Physical Layer: Concerned with the transmission of raw data over physical media.
- Layer 2: Data Link Layer: Ensures reliable communication between directly connected devices.
- Layer 3: Network Layer: Facilitates end-to-end packet delivery and routing across interconnected networks.
- Layer 4: Transport Layer: Provides reliable data transfer and error recovery mechanisms.
- Layer 5: Session Layer: Manages communication sessions and data exchange between networked applications.
- Layer 6: Presentation Layer: Standardizes data formats and encryption methods.
- Layer 7: Application Layer: Provides network services and interfaces for user applications.
The modular structure of the OSI model fosters interoperability, scalability, and ease of troubleshooting in network design and implementation.
Encapsulation: Safeguarding Data Integrity and Routing Efficiency
Encapsulation stands as a foundational concept in networking, serving as a mechanism to package data along with relevant control information for efficient transmission across networks. This process not only ensures data integrity but also enhances routing efficiency by providing essential metadata for effective packet delivery. In this in-depth article, we explore the intricacies of encapsulation in networking, dissecting its components, elucidating its significance, and providing real-world examples to illustrate its application in safeguarding data and optimizing network performance.
Understanding Encapsulation
Encapsulation in networking refers to the process of wrapping data with header and trailer information at each protocol layer as it traverses the network stack. Each layer adds its own header and, optionally, trailer to the data payload, creating a layered structure that facilitates data transmission and reception.
Components of Encapsulation
Encapsulation involves several key components, each serving a distinct purpose in the data transmission process
Data Payload
The data payload constitutes the actual information being transmitted across the network. It may include text, images, audio, video, or any other form of digital content.
Header
The header contains metadata essential for packet routing, error detection, and protocol identification. It typically includes fields such as source and destination addresses, protocol type, packet length, time-to-live (TTL), and checksum.
Trailer (Optional)
In some cases, a trailer section may be appended to the packet, containing additional control information or error detection codes. While not always present, trailers can enhance the reliability and integrity of data transmission
Significance of Encapsulation
Encapsulation plays a critical role in networking for the following reasons:
- Data Integrity: By encapsulating data within headers, encapsulation mechanisms provide error detection and correction capabilities to ensure data integrity during transmission. Checksums and other error detection codes enable recipients to verify the integrity of received data and detect any potential transmission errors.
- Routing Efficiency: Encapsulation facilitates routing efficiency by providing essential routing information within packet headers. Source and destination addresses, along with other routing parameters, enable routers to make forwarding decisions and route packets along the most efficient path to their destination.
- Protocol Compatibility: Encapsulation enables protocol compatibility by defining a standardized packet format that can be interpreted by different networking devices and protocols. Regardless of the underlying hardware or software, devices can exchange encapsulated packets using a common set of protocols and conventions.
Examples of Encapsulation
To better understand the concept of encapsulation, consider the following examples:
- Ethernet Frame Encapsulation: In Ethernet networks, data is encapsulated within Ethernet frames for transmission across physical media. Each Ethernet frame consists of a header containing source and destination MAC addresses, along with a payload containing the data to be transmitted.
- IP Packet Encapsulation: Within the Internet Protocol (IP) suite, data is encapsulated within IP packets for routing across interconnected networks. The IP header contains source and destination IP addresses, protocol type, packet length, TTL, and checksum, among other fields.
- TCP Segment Encapsulation: In TCP/IP networks, data is encapsulated within TCP segments for reliable transmission between endpoints. The TCP header contains sequence numbers, acknowledgment numbers, window sizes, checksums, and other control information necessary for reliable data delivery.
Conclusion
In conclusion, networking protocols, layers, and encapsulation mechanisms form the backbone of modern communication systems, enabling the seamless exchange of data across diverse environments. By understanding the nuances of protocols, adhering to layered design principles, and leveraging encapsulation techniques, network engineers can design robust, scalable, and interoperable networks capable of meeting the evolving demands of our interconnected world. This extensive exploration has provided readers with a deep understanding of these fundamental networking concepts, empowering them to navigate the complexities of modern networking with confidence and proficiency.







