The Hypertext Transfer Protocol (HTTP) and its secure counterpart, Hypertext Transfer Protocol Secure (HTTPS), underpin the seamless exchange of information that defines our web experience. Whether browsing articles, conducting online transactions, or collaborating remotely, an understanding of HTTP/HTTPS mechanics is essential for both web developers and discerning users. In this post, we will be demystifying HTTP and HTTPS.
HTTP: The Language of the Web

At its core, HTTP provides a structured framework for communication between clients (typically web browsers) and servers. Consider this analogy:
- Client (Web Browser): A discerning shopper with a specific list.
- Server: A well-organized storehouse of digital resources.
- HTTP: The mutually understood protocol governing interactions between shopper and store.
The Discerning Shopper (Client/Web Browser)
- Diverse Needs: Just as shoppers have unique requirements, web browsers can demand various digital resources. Some browsers might need text-based HTML for an article, others seek videos, images, or even downloadable software.
- Capabilities and Preferences: Similar to how shoppers convey preferences (“organic products only”), browsers communicate their capacities through HTTP headers. Headers may describe supported file formats, acceptable languages, and even whether they should access a cached (older, stored) version of the resource.
- Identity Badges: Just as some stores need membership verification, specific servers require client authentication. Using authentication mechanisms within HTTP, web browsers can offer login credentials, digital certificates, or API keys to unlock access to restricted resources.
The Organized Storehouse (Server)
- Shelves and Sections: A server meticulously classifies its digital resources. This resembles a store organizing products logically. Websites utilize a folder-like structure (directories and subdirectories) to arrange HTML files, images, style sheets, etc.
- Inventory Management: Servers, like stores, monitor stock availability. When a resource is permanently gone, it returns an HTTP ‘404 Not Found’ (equivalent to an out-of-stock item). Likewise, ‘503 Service Unavailable’ might represent a temporary closure, just like a store’s occasional downtime.
- Specialized Departments: Stores often have designated areas (electronics, furniture, apparel, etc.). Similarly, servers can house multiple web applications. A single server might manage a company’s blog, e-commerce system, and customer support software under different sections of its file system.
The Protocol for Interaction (HTTP)
- The Order Form (HTTP Request):
- “I need, please…”: The HTTP Method (‘GET’, ‘POST’, etc.) acts like the shopper stating their intent – seeking an item, trying on clothing, etc.
- “This exact Item”: The target URL pinpoints the resource location akin to a shopper mentioning product ID or its shelf location.
- “I speak these languages…”: Headers reveal client capabilities (browser type, accepted languages, desired data formats, like a shopper stating product preferences and preferred communication)

- The Store’s Reply (HTTP Response):
- “Here you go/We don’t have that/Something went wrong…” Status codes tell the shopper the request result – item found, not in stock, or whether some unexpected problem occurred in the store.
- “Additional Info” Headers include resource-specific data (file size, last modification date), content type (for browsers to properly render it), and server-related information (much like a store’s return policy or brand identifier might be attached).
- “The Item Itself (Payload)” If successful, the HTTP response contains the sought-after item (HTML text, image file, video, etc.), just as a shopper leaves with their purchased goods.

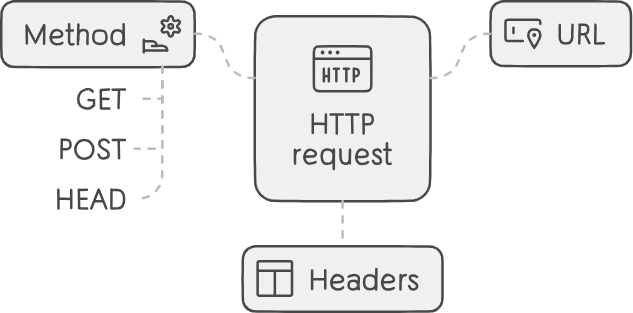
HTTP Requests: Precise Instructions for Resource Retrieval
An HTTP request acts as a meticulous order form transmitted from the client to the server. Key components include:
- Method: Specifies the desired action on the server. Popular methods are:
- GET: Fetches a resource.
- POST: Submits data for processing (e.g., forms).
- HEAD: Requests similar information to GET but without the actual resource data.
- URL (Uniform Resource Locator): Pinpoints the exact location of the requested resource.
- Headers: Offer supplemental details about the client’s capabilities and preferences (language, supported media types, caching instructions, etc.).
Let’s illustrate a real-world HTTP request-response exchange when you load a simple webpage. We’ll use a basic HTML resource for ease of understanding.
Scenario: You type www.example.com into your browser’s address bar and hit Enter.
1. The HTTP Request
Your browser constructs an HTTP request resembling this:
GET /index.html HTTP/1.1
Host: www.example.com
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0 (Your OS and browser details here)
Accept-Language: en-US,en;q=0.5
Connection: keep-alive 
Explanation:
- GET /index.html HTTP/1.1: Instructs the server to fetch the ‘index.html’ file using the HTTP 1.1 protocol.
- Host: www.example.com: Specifies the target server’s domain name.
- Accept: Indicates the browser understands HTML, XHTML, XML (with varying preferences), and general content types.
- User-Agent: Information detailing your browser and operating system.
- Accept-Language: Prefers responses in English.
- Connection: keep-alive: A request to maintain an open connection for potential subsequent requests.
2. The HTTP Response
The server at www.example.com processes the request and sends an HTTP response similar to this:
HTTP/1.1 200 OK
Date: Mon, 13 Feb 2024 16:45:00 GMT
Server: Apache/2.4.54
Content-Length: 325
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html>
<head>
<title>Example Website</title>
</head>
<body>
<h1>Welcome to My Website</h1>
<p>This is a simple webpage.</p>
</body>
</html>
Explanation:
- HTTP/1.1 200 OK: Success! The ‘index.html’ file was found and returned.
- Date: Date and time stamp of the response.
- Server: Software powering the web server.
- Content-Length: Indicates the size of the HTML content in bytes.
- Content-Type: Specifies the format of the returned data (HTML with UTF-8 character encoding).
- (HTML Content): The actual HTML code that your browser then renders as the webpage.
Visualizing the Exchange
- Browser Tools: Your browser’s developer console (Network tab) showcases such exchanges for every resource loaded on a page.
- Command-Line Tools: Using
curlwith a verbose flag reveals details:curl -v http://www.example.com
Important Notes:
- Real-world exchanges may involve numerous requests for a single webpage (CSS, JavaScript files, images, etc.).
- Headers can expand extensively to include cookies, caching directives, and security-related information.
The structure of an HTTP request provides a framework for precise communication between client and server. Let’s dissect its key components:
Method: The Verb that Dictates Actions
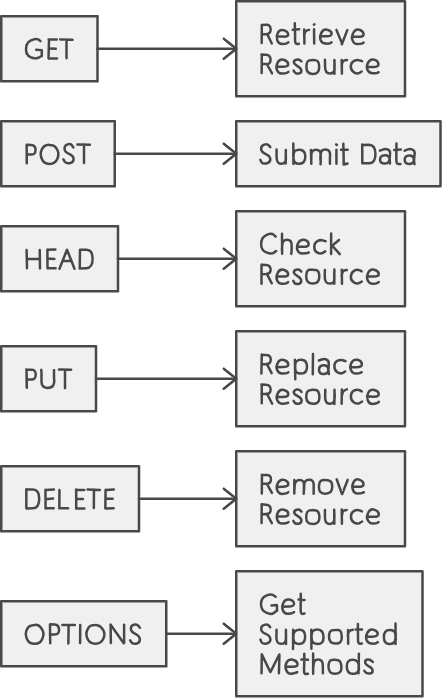
- GET: The cornerstone of web interaction. Requests that the server retrieve and return a specific resource. Ideally, GET requests should be idempotent – repeated identical requests don’t change the state of the server.
- POST: The workhorse for submitting data to the server. Used for actions like form submissions, creating new resources, or initiating processes with potential side effects on the server.
- HEAD: Echoes a GET request, but requests only the headers of the response, not the actual resource. Useful for checking resource existence, size, or last modification without downloading the full content.
- PUT: Replaces an existing resource entirely with the content provided in the request payload.
- DELETE: Signals the server to remove a specified resource.
- OPTIONS: Requests information about supported communication methods for a specific resource. Used to understand what actions can be performed and their requirements.
URL (Uniform Resource Locator): The Exact Address
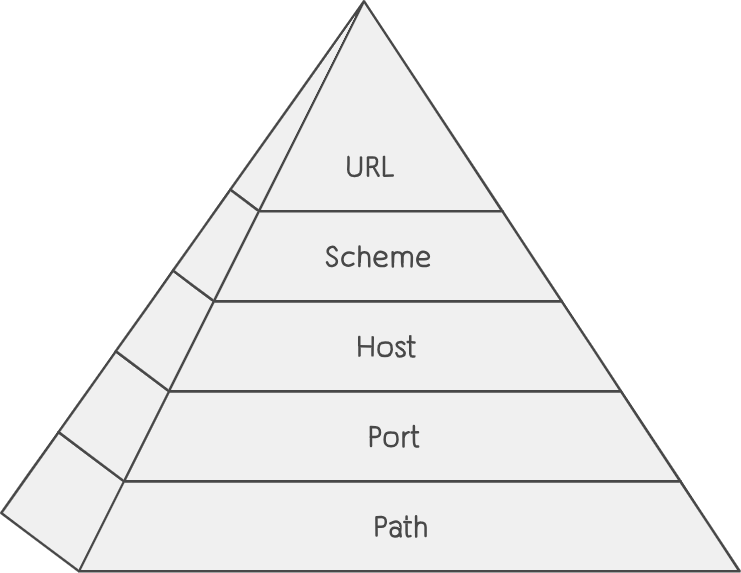
- Scheme: Indicates the protocol. Usually
http://orhttps://. - Host: The domain name or IP address of the server (e.g.,
www.example.com). - Port: Optional; designates the network port of the service (e.g.,
:80for HTTP,:443for HTTPS). - Path: Specifies the hierarchical location of the resource within the server (e.g.,
/blog/article.html). - Query Parameters: Key-value pairs appended after a
?(e.g.,/search?query=http). They pass additional data to the server.
Headers: Contextual Metadata
HTTP headers present a treasure trove of details to facilitate the request-response cycle. Some common headers include:
- Accept: Informs the server about the media types the client understands (e.g.
text/html,application/json). - Content-Type: Denotes the format of the data within a POST or PUT request’s body.
- Authorization: Carries credentials for authentication/authorization purposes.
- Cache-Control: Instructs browsers and proxies on how to cache responses.
- Cookie: Small pieces of data stored by the browser for maintaining state.
HTTP Responses: Delivery of Requested Resources
The server’s reply takes the form of an HTTP response. Essential elements within this response include:
- Status Code: A numerical indicator signaling the request outcome:
- 2xx Success: Example: 200 OK for a fulfilled request.
- 4xx Client Errors: Examples: 404 Not Found, 403 Forbidden.
- 5xx Server Errors: Example: 500 Internal Server Error.
- Headers: Convey metadata like content type, caching directives, and server information.
- Body (Payload): Contains the requested resource (HTML, images, JSON data, etc.) if successfully retrieved.
Status codes form an integral part of HTTP responses. Let’s categorize them:
- 1xx (Informational): Communicates provisional updates about the request process.
- 2xx (Success): Signals that the request was received, understood, and successfully processed.
200 OK: Classic success code.201 Created: New resource created on the server.
- 3xx (Redirection): Indicates the client needs to follow further steps to complete the request.
301 Moved Permanently: Permanently redirects to a new resource location.
- 4xx (Client Error): Implies the fault lies with the client’s request.
400 Bad Request: Syntax error, or the server couldn’t understand the request.401 Unauthorized: Missing or invalid authentication credentials.403 Forbidden: The client doesn’t have permission to access the resource.404 Not Found: The requested resource doesn’t exist.
- 5xx (Server Error): Indicates issues on the server side prevented request fulfillment.
500 Internal Server Error: Generic catch-all for unanticipated server problems.503 Service Unavailable: Server may be overloaded or under maintenance.
Looking Forward: HTTP/2 and HTTP/3
HTTP has gone through iterations:
- HTTP/2: Significant improvements like binary framing of data, multiplexing connections, and header compression address limitations in HTTP/1.1
- HTTP/3: Built on top of QUIC (a new transport protocol), further reduces latency and stream blocking issues compared to its predecessors.
HTTPS: Beyond Padlocks and Prefixes

While most users easily recognize the padlock symbol and the “https://” prefix as signs of site security, HTTPS involves a fascinating orchestration of cryptographic components to achieve its protection goals.
Deep Dive into HTTPS Mechanics
- The TLS Handshake: Establishing a Secure ‘Tunnel’
- Client Hello: The web browser greets the server with a “Client Hello” message. This message outlines the supported cipher suites (algorithms for encryption and authentication) and a random string of bytes (client random).
- Server Hello: The server replies with a “Server Hello,” selecting a cipher suite, its digital certificate, and another random string of bytes (server random).
- Certificate Validation: The browser rigorously verifies the server’s certificate, issued by a trusted Certificate Authority (CA). This assures that the server rightfully owns the domain name it claims.
- Pre-Master Secret & Session Keys: Both client and server cleverly use the previously exchanged random values and the server’s public key (within the certificate) to generate a “pre-master secret.” This pre-master secret is then used to derive symmetric session keys – unique keys for encrypting and decrypting data in this specific session.

- Encrypted Communication: Data in Disguise
- Symmetric Encryption: HTTPS now shifts away from public-key cryptography for the bulk of data protection. Using the previously established session keys, both client and server utilize a chosen symmetric encryption algorithm (e.g., AES) to encrypt all subsequent application data exchanged within the session. This is fast and efficient.
- Message Authentication Codes (MACs): Alongside each encrypted chunk of data, a Message Authentication Code (MAC) is calculated and attached. This ensures data integrity – the recipient can calculate the MAC on their end and confirm whether the received data exactly matches the one that was sent, thwarting modifications.

Breaking Down the Analogy
- Encryption: Not merely scrambling conversations, but more akin to using a secret language code that only the shopper and cashier understand. Even if overheard, the conversation is gibberish.
- Authenticating the Store: Our security guard performs more than just a visual check for a store sign. They meticulously vet official identification certificates from reputable institutions (akin to Certificate Authorities), ensuring they’re dealing with the genuine store.
- Preventing Tampering in Transit: Consider them an armored transporter with tamper-proof seals. HTTPS utilizes both encryption and integrity checks to detect and reject any attempt to modify data en route.
The Price of Security
HTTPS doesn’t come without trade-offs:
- Performance Overhead: The TLS handshake and the ongoing encryption and decryption processes create an overhead (typically minor for modern systems).
- Setup and Maintenance: Web servers must obtain and correctly configure digital certificates from trusted CAs, involving some initial cost and administrative effort.
Spotting the Gaps
HTTPS, even when correctly implemented, offers safeguards specific to browser-server communication:
- Beyond a Single Site: An HTTPS site might still host elements loaded insecurely over HTTP (mixed content). These can compromise overall security.
- Malware: HTTPS won’t protect you from malware already on your device.
- Phishing: HTTPS only authenticates the server, not the authenticity of the content. Phishing sites masquerading as legitimate ones can also deploy HTTPS to create a false sense of security.
The Informed Web User: Your Role
While HTTPS plays a crucial part in internet security, user vigilance remains essential. Keep these guidelines in mind:
- Look for the HTTPS indicators, ensuring sites you provide sensitive information to (banking, social media, etc.) use HTTPS.
- Be cautious of ‘mixed content’ warnings displayed by your browser.
- Be wary of any links from dubious sources, irrespective of HTTPS.
HTTP vs. HTTPS: When to Use Which
- HTTP: Acceptable for situations where:
- Data confidentiality is not paramount
- You desire raw performance over absolute security (however, HTTP/2 mitigates some speed disadvantages)
- HTTPS: A must when handling sensitive data or performing interactions like:
- E-commerce and financial transactions
- User login and authentication flows
- Exchange of any personally identifiable information
- Situations where establishing user trust is essential







