In the realm of cybersecurity, tools play a crucial role in defending networks, identifying vulnerabilities, and understanding the ever-changing landscape of digital threats. Among these tools, Nmap emerges as a cornerstone, offering unparalleled capabilities in network scanning and security auditing. This blog post is about Nmap unveiled. Developed by Gordon Lyon, also known as Fyodor Vaskovich, Nmap has evolved into an essential utility for cybersecurity professionals, researchers, and enthusiasts worldwide. This comprehensive guide aims to delve deeply into Nmap’s functionalities, techniques, practical applications, and best practices, empowering users to leverage its power effectively in safeguarding network infrastructures and enhancing cybersecurity posture.
Understanding Nmap: An Overview
At its core, Nmap, short for “Network Mapper,” is an open-source tool designed to explore networks, discover hosts, enumerate services, and identify potential vulnerabilities. Initially released in 1997, Nmap has undergone significant development, expanding its feature set, improving performance, and adapting to the evolving demands of the cybersecurity landscape. Leveraging a combination of advanced scanning techniques, protocol implementations, and scripting capabilities, Nmap remains at the forefront of network reconnaissance and security auditing.
The Fundamentals of Network Scanning
Network scanning forms the foundation of Nmap’s functionality, enabling users to gather information about hosts, services, and network configurations. Nmap employs a variety of scanning techniques, each tailored to specific objectives and environments:
- TCP Connect Scanning: This method establishes a full TCP connection with target ports, providing reliable results but also raising the risk of detection by intrusion detection systems (IDS) and firewalls.
- SYN Stealth Scanning: SYN scanning involves sending SYN packets to target ports without completing the full TCP handshake, offering stealthier reconnaissance capabilities.
- UDP Scanning: UDP scanning entails sending UDP packets to target ports and analyzing their responses, although it’s generally slower and less reliable compared to TCP scans.
- ACK Scanning: ACK scanning examines how target hosts respond to ACK packets, primarily used to determine firewall configurations and filter rules.
- Operating System Detection: Nmap can infer the operating system running on target hosts by analyzing subtle differences in their TCP/IP stack implementations and responses to specific probes.
Installation and Configuration
Before exploring Nmap’s capabilities, it’s essential to install and configure the tool on your system. Nmap is compatible with a wide range of operating systems, including Linux, Windows, macOS, and BSD variants. Installation methods vary depending on the platform, but packages are readily available from official sources, package repositories, and community-maintained repositories.
Once installed, users can customize Nmap’s behavior, adjust scanning parameters, and leverage additional features through configuration files and command-line options. Understanding these configurations allows users to optimize scan performance, enhance stealth capabilities, and tailor scans to specific environments and objectives.
Practical Applications of Nmap
Nmap’s versatility extends far beyond basic network discovery, encompassing a wide range of cybersecurity tasks and applications:
- Network Inventory: Nmap enables administrators to create comprehensive inventories of devices, services, and network assets. By scanning IP ranges, subnets, and network segments, administrators can identify active hosts, open ports, and associated services, facilitating network management and resource allocation.
- Vulnerability Assessment: Nmap’s scripting engine, coupled with its extensive database of detection signatures, allows users to conduct comprehensive vulnerability assessments. Custom scripts can be developed to identify specific vulnerabilities, misconfigurations, and security weaknesses within target systems and applications.
- Penetration Testing: Ethical hackers, security consultants, and penetration testers rely on Nmap to assess the security posture of target networks and systems. By identifying open ports, services, and potential attack vectors, testers can simulate real-world scenarios, assess defensive measures, and provide actionable insights to stakeholders.
- Network Mapping and Visualization: Nmap’s graphical output options enable users to create visual representations of network topologies, relationships between hosts, and service dependencies. These visualizations aid in understanding complex network architectures, identifying critical assets, and visualizing attack surfaces for strategic decision-making.
- Security Auditing and Compliance: Nmap serves as a valuable tool for conducting security audits, compliance assessments, and regulatory evaluations. By scanning network infrastructures, organizations can identify security gaps, measure adherence to security policies, and prioritize remediation efforts to mitigate risks and ensure compliance with industry standards and regulations.
Best Practices and Considerations
While Nmap empowers users with advanced scanning capabilities, its usage must be approached with caution and responsibility. Adhering to best practices ensures ethical conduct, legal compliance, and effective utilization of Nmap’s features:
- Obtain Proper Authorization: Before conducting network scans, ensure that you have explicit permission from the network owner, administrator, or authorized stakeholders. Unauthorized scanning can lead to legal repercussions, damage relationships, and disrupt network operations.
- Minimize Impact and Noise: Configure Nmap to operate within acceptable bandwidth and resource limits to avoid disrupting network operations, causing service interruptions, or triggering alarms on intrusion detection systems (IDS) and firewalls. Utilize stealth scanning techniques, timing options, and rate limiting to minimize network noise and avoid detection.
- Stay Informed and Updated: Keep abreast of Nmap’s latest features, updates, and vulnerabilities by monitoring official channels, security advisories, and community forums. Regularly update your Nmap installation to ensure access to new features, bug fixes, and patches for known security issues.
- Document Findings and Observations: Maintain detailed documentation of scanning results, methodologies, observations, and remediation recommendations for future reference, analysis, and reporting. Documentation serves as a valuable resource for network troubleshooting, incident response, forensic investigations, and security audits.
Example: Scanning a Target with Nmap
Let’s walk through a practical example of how to use Nmap to scan a target host. In this scenario, we’ll perform a TCP SYN scan on a target host with the IP address 192.168.1.100.
- Open Terminal/Command Prompt: Begin by opening a terminal window (Linux/macOS) or command prompt (Windows) on your system.
- Execute Nmap Command: In the terminal/command prompt, type the following command to perform a TCP SYN scan on the target host:
nmap -sS 192.168.1.100Explanation of Command Options:
-sS: This option specifies the TCP SYN scan technique, which sends SYN packets to the target ports without completing the full TCP handshake.192.168.1.100: Replace this IP address with the actual IP address of the target host you want to scan.
- Review Scan Results: After executing the command, Nmap will initiate the scan and display the results in the terminal/command prompt window. The output will include information about open ports, services running on those ports, and potentially the operating system of the target host.
Here’s an example of what the Nmap output might look like:
Starting Nmap 7.91 ( https://nmap.org ) at
2024-01-28 12:00 EST
Nmap scan report for 192.168.1.100
Host is up (0.0030s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https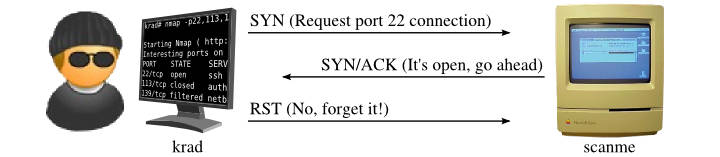
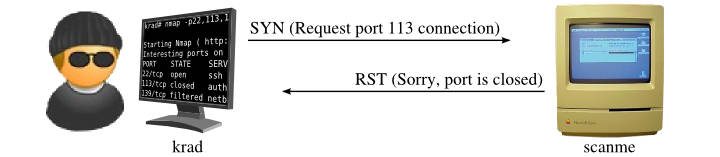
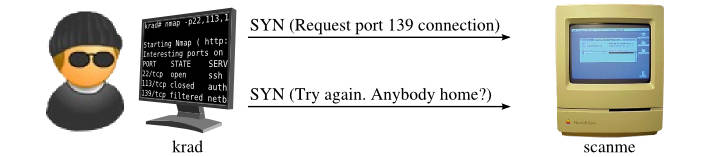
How Nmap interprets responses to a SYN probe
| Probe Response | Assigned State |
|---|---|
| TCP SYN/ACK response | open |
| TCP RST response | closed |
| No response received (even after retransmissions) | filtered |
| ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) | filtered |
Conclusion
In conclusion, Nmap stands as a testament to the power of open-source innovation and collaborative development in the cybersecurity community. Its robust feature set, flexible scanning techniques, and extensive documentation make it an indispensable tool for network reconnaissance, security auditing, and threat intelligence.
By mastering the fundamentals of Nmap, adhering to best practices, and embracing a culture of continuous learning, cybersecurity professionals and enthusiasts can harness its power to uncover hidden vulnerabilities, strengthen defenses, and safeguard critical assets in an ever-evolving threat landscape.
In the dynamic realm of cybersecurity, Nmap serves as a beacon of insight and vigilance, empowering defenders to navigate the intricate labyrinth of network security with confidence, precision, and resilience. Through responsible usage and ethical conduct, Nmap users contribute to the collective effort of securing digital infrastructure and safeguarding the integrity of information in an interconnected world.







